- Pro
- Security
A legitimate feature is being abused to hide phishing emails
Comments (0) ()When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
 (Image credit: weerapatkiatdumrong / Getty Images)
(Image credit: weerapatkiatdumrong / Getty Images)
- Attackers abused Mimecast’s URL‑rewriting feature to mask malicious links in phishing emails
- More than 40,000 emails hit 6,000+ organizations, especially consulting, tech
- Campaign bypassed filters globally, with most victims in the US, though Mimecast says no flaw exists
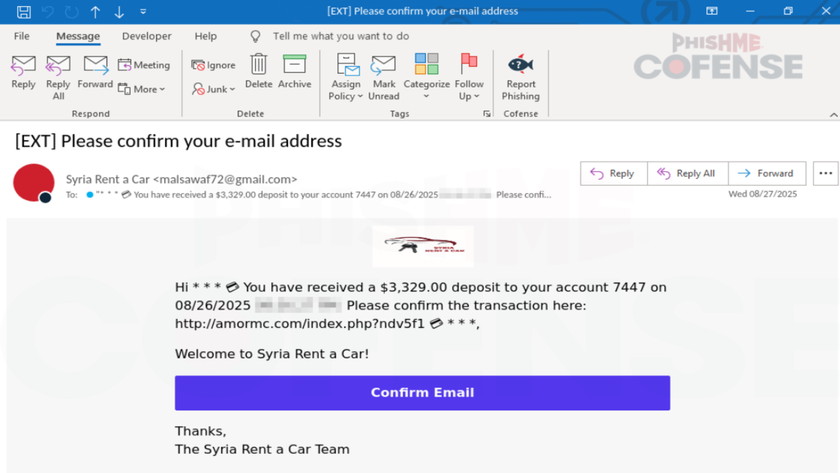
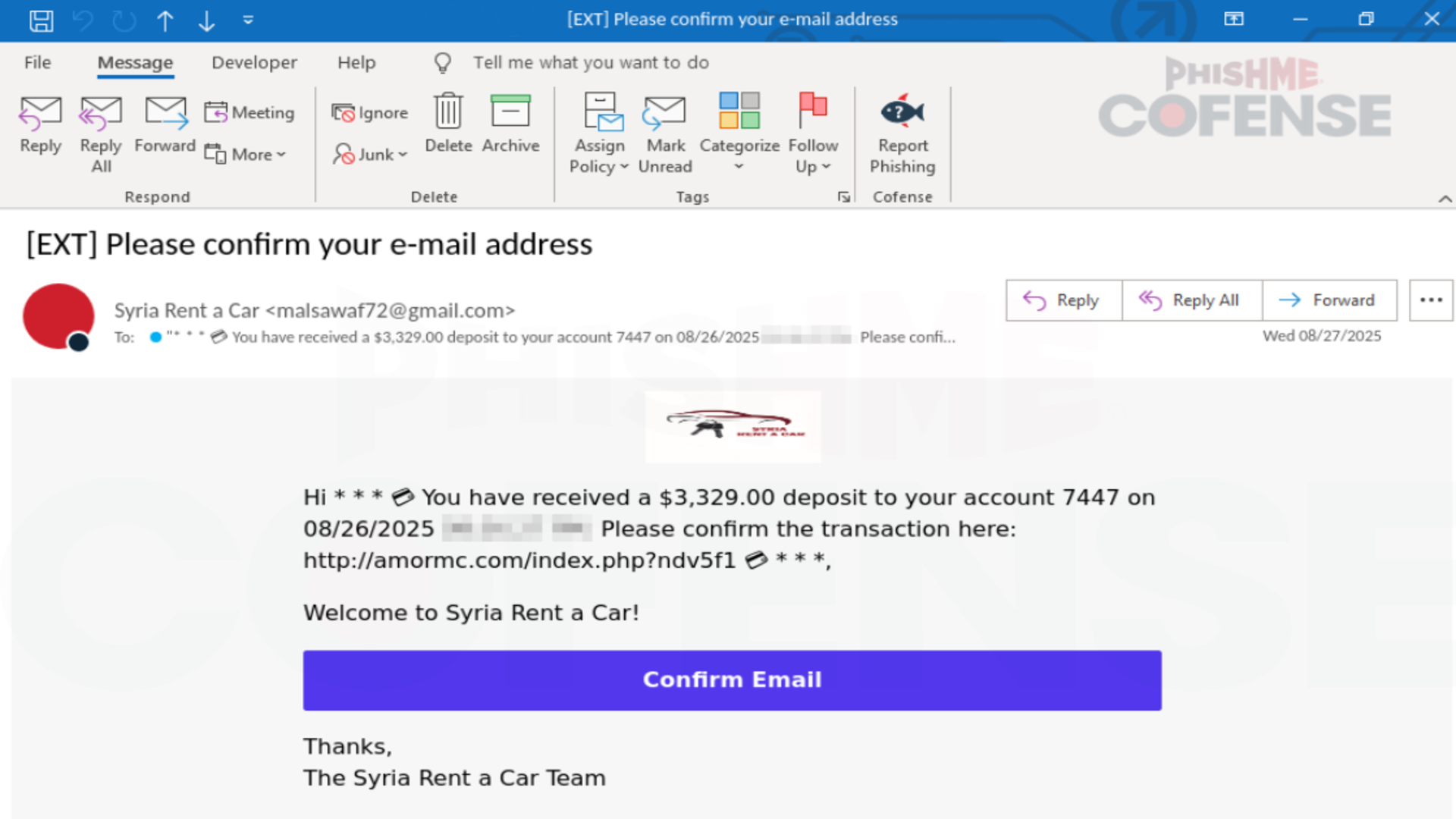
Cybercriminals are abusing a legitimate Mimecast feature to deliver convincing phishing emails to their victims - at scale.
This is according to cybersecurity researchers Check Point, who claim to have seen more than 40,000 such emails being sent to over 6,000 organizations around the world, in a span of merely two weeks.
First, the crooks would create messages that closely resemble email notifications from reputable brands (SharePoint, DocuSign, or other e-signature notices), paying attention to the details such as logos, subject lines, and display names. Nothing in the messages stands out from routine notification emails.
You may like-
 Microsoft 365 users targeted by major new phishing operation - here's how to stay safe
Microsoft 365 users targeted by major new phishing operation - here's how to stay safe
-
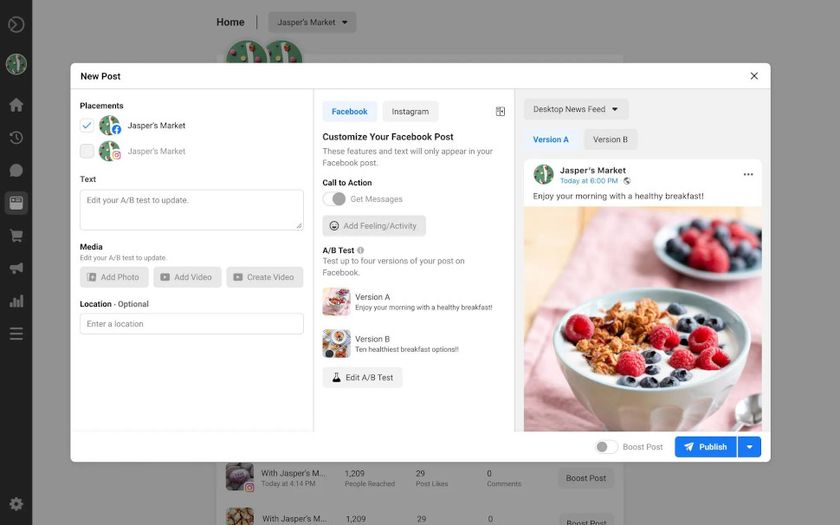 Fake Facebook Business pages are bombarding users with phishing messages - so what can be done?
Fake Facebook Business pages are bombarding users with phishing messages - so what can be done?
-
 Microsoft's branding power is being used by criminals to funnel victims to tech support scam centers - here's what you need to know
Microsoft's branding power is being used by criminals to funnel victims to tech support scam centers - here's what you need to know

Catch the price drop- Get 30% OFF for Enterprise and Business plans
The Black Friday campaign offers 30% off for Enterprise and Business plans for a 1- or 2-year subscription. It’s valid until December 10th, 2025. Customers must enter the promo code BLACKB2B-30 at checkout to redeem the offer.
View DealConsulting, tech, and real estate targeted
At the same time, they would build phishing landing pages that capture credentials or deliver malware. These URLs are wrapped behind one or more legitimate redirect and tracking services, in this case - Mimecast.
Because this service rewrites links to route through a trusted domain, attackers submit their malicious links so the final email shows a Mimecast domain instead of the real destination.
As a result, phishing emails successfully move past email security solutions and filters, and land directly into their victim’s inboxes.
Check Point says that numerous industries were hit by this campaign, but a few - where contracts and invoices exchange is an everyday thing - were hit particularly hard. Those include consulting, technology, and real estate. Other notable mentions include healthcare, finance, manufacturing, and government.
Are you a pro? Subscribe to our newsletterContact me with news and offers from other Future brandsReceive email from us on behalf of our trusted partners or sponsorsBy submitting your information you agree to the Terms & Conditions and Privacy Policy and are aged 16 or over.The majority of the victims are located in the US (34,000), followed by Europe (4,500), and Canada (750).
Mimecast stressed that this is not a vulnerability, but rather a legitimate feature, that is being abused.
“The attacker campaign described by Check Point exploited legitimate URL redirect services to obfuscate malicious links, not a Mimecast vulnerability. Attackers abused trusted infrastructure – including Mimecast’s URL rewriting service – to mask the true destination of phishing URLs. This is a common tactic where criminals leverage any recognized domain to evade detection.”
Via Cybernews
 The best antivirus for all budgetsOur top picks, based on real-world testing and comparisons
The best antivirus for all budgetsOur top picks, based on real-world testing and comparisons➡️ Read our full guide to the best antivirus1. Best overall:Bitdefender Total Security2. Best for families:Norton 360 with LifeLock3. Best for mobile:McAfee Mobile Security
Follow TechRadar on Google News and add us as a preferred source to get our expert news, reviews, and opinion in your feeds. Make sure to click the Follow button!
And of course you can also follow TechRadar on TikTok for news, reviews, unboxings in video form, and get regular updates from us on WhatsApp too.
Sead FadilpašićSocial Links NavigationSead is a seasoned freelance journalist based in Sarajevo, Bosnia and Herzegovina. He writes about IT (cloud, IoT, 5G, VPN) and cybersecurity (ransomware, data breaches, laws and regulations). In his career, spanning more than a decade, he’s written for numerous media outlets, including Al Jazeera Balkans. He’s also held several modules on content writing for Represent Communications.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
Logout Read more Microsoft 365 users targeted by major new phishing operation - here's how to stay safe
Microsoft 365 users targeted by major new phishing operation - here's how to stay safe
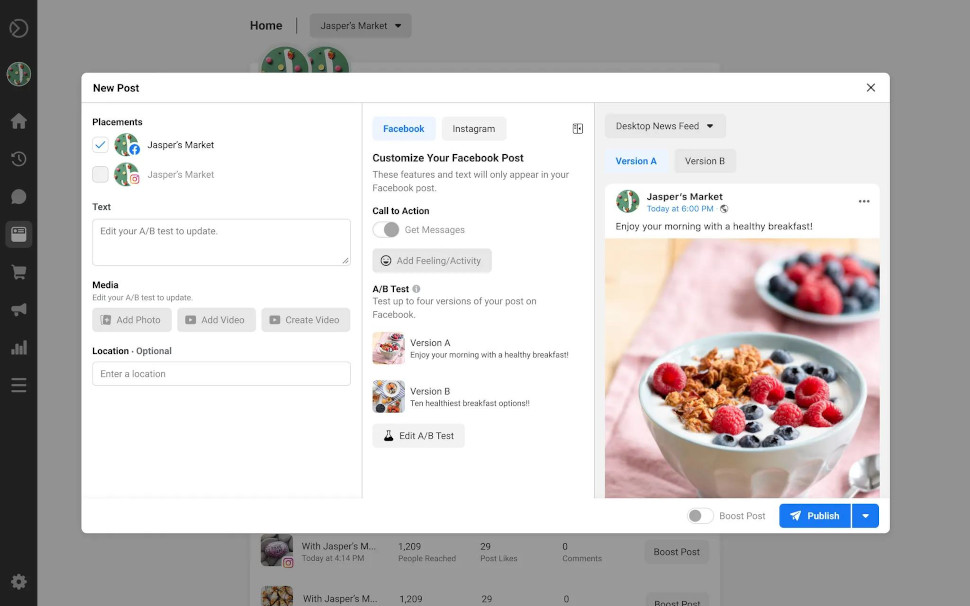 Fake Facebook Business pages are bombarding users with phishing messages - so what can be done?
Fake Facebook Business pages are bombarding users with phishing messages - so what can be done?
 Microsoft's branding power is being used by criminals to funnel victims to tech support scam centers - here's what you need to know
Microsoft's branding power is being used by criminals to funnel victims to tech support scam centers - here's what you need to know
 This new phishing kit turns PDF files into malware - here's how to stay safe
This new phishing kit turns PDF files into malware - here's how to stay safe
 Hackers set to weaponize harmless legit PDFs using new tools, with experts saying that combining it with SpamGPT could be a huge game-changer
Hackers set to weaponize harmless legit PDFs using new tools, with experts saying that combining it with SpamGPT could be a huge game-changer
 Fake VPN checker tool lets hackers bypass antivirus protections
Latest in Security
Fake VPN checker tool lets hackers bypass antivirus protections
Latest in Security
 ICO levies £1.2 million fine against LastPass — data breach compromised info on 1.6 million users
ICO levies £1.2 million fine against LastPass — data breach compromised info on 1.6 million users
 OpenAI admits new models likely to pose 'high' cybersecurity risk
OpenAI admits new models likely to pose 'high' cybersecurity risk
 Google releases emergency fix for yet another zero-day
Google releases emergency fix for yet another zero-day
 Russian airline hack came through third-party tech vendor
Russian airline hack came through third-party tech vendor
 16TB of corporate intelligence data exposed in one of the largest lead-generation dataset leaks
16TB of corporate intelligence data exposed in one of the largest lead-generation dataset leaks
 Proton Pass just made it even easier for developers to retrieve secrets — and that's a win for everyone involved
Latest in News
Proton Pass just made it even easier for developers to retrieve secrets — and that's a win for everyone involved
Latest in News
 ChatGPT 5.2 is here and ready to show you professional AI
ChatGPT 5.2 is here and ready to show you professional AI
 Mullvad retires OpenVPN support on desktop, pushing all users to WireGuard
Mullvad retires OpenVPN support on desktop, pushing all users to WireGuard
 Switzerland will revise proposed law change after backlash from tech industry
Switzerland will revise proposed law change after backlash from tech industry
 How to watch Celtic vs AS Roma: Europa League 2025/26 free stream, TV channels, kick-off time
How to watch Celtic vs AS Roma: Europa League 2025/26 free stream, TV channels, kick-off time
 ‘They gave us the iPhone camera’: F1 producer Jerry Bruckheimer on Apple’s ‘phenomenal’ involvement in the movie’s production
‘They gave us the iPhone camera’: F1 producer Jerry Bruckheimer on Apple’s ‘phenomenal’ involvement in the movie’s production
 The Galaxy Z TriFold has a neat PC trick that could justify its price tag
LATEST ARTICLES
The Galaxy Z TriFold has a neat PC trick that could justify its price tag
LATEST ARTICLES- 1I wasn’t convinced there was a need for the LG StanByMe 2 TV – but I’m completely sold on this rollable display after 3 weeks with it
- 2Which brand has the best pet hair tool? I tested a whole bunch – here are the results
- 3ChatGPT 5.2 is here and all about being a better thinker – here are the 3 things you need to know
- 4Mysterious 88-core AMD CPU surfaces on eBay, and here's why I think it's the start of something big
- 5OpenAI admits new models likely to pose 'high' cybersecurity risk
